Based on my lesson today I'll be giving my notes on a basic introduction to Ethernet.
I'll be covering:
1. The evolution of Ethernet
2. CSMA/CD - The Essence of Ethernet technology
3. Methods of Communicating in the LAN
4. The official explanation of a MAC address
Here is a short background on what we know as Ethernet:
1973: Xerox invents Ethernet (3 Mbps)
1982: Ethernet standardized between vendors (10 Mbps)
1995: Fast Ethernet emerges (100 Mbps)
2000: Gigabit Ethernet emerges (1000 Mbps)
2002: 10 Gigabit Ethernet emerges (10000 Mbps)
2007: 100 Gigabit Ethernet emerges (100000 Mbps)
How about a short review on common storage terms we face everyday?
1 Byte = 1 character (For you C programmers out there, its like char temp = 'C')
1024 Bytes = 1 Kilobyte
1024 Kilobytes = 1 Megabyte
1024 Megabytes = 1 Gigabyte
1024 Gigabytes = 1 Terabyte
and so forth....
However when we talked about the Ethernet speeds as mentioned earlier, we used Mbps.... Mbps here stands for mega bits per second.
You may ask....well then why did you just give us that that explanation using Bytes?
Byte vs bit? What's the difference?
All you need to know is that 1 byte is equal to 8 bits. Furthermore all of you probably know that a bit is just a representation of 1 or 0.
Therefore:
1 Byte = 8 bits
1024 Bytes = 1 Kilobyte = (1024 * 8 = 8192) bits
and so forth....
So remember when work with networks, we think of BITS not BYTES!!!
-----
With relation to the OSI model, Ethernet maps to the bottom two layers. That means it is both a data link and physical entity.
On the data link layer, it is further sub-divided into the Logical Link Control Layer (LLC) and the Media Access Control Layer (MAC).

Now don't worry about the sub-division here, as its very logical.
The MAC layer is what we are accustomed to so far, that is the MAC addresses we have been using so far when we speak over layer 2.
Now the LLC layer is a bit new to us at the moment. This layer allows us to choose which direction we are going to be going into the network layer. Let us expound on this...
The network layer, as we know it so far, uses IP addresses to communicate. However you can have other types of network layer communication. Some of these include IPSX, Apple-talk and others. The LLC field allows us to choose IP on the network layer when we are using TCP/IP to communicate.
Therefore when a packet arrives to a machine and its moving from the bottom to the top of the OSI model, the LLC portion of the data link layer will decide whether or not to send the packet to IP or some other addressing mechanism.
With regards to the physical standards, Ethernet specifies several types of communication. These include cat 5 cables, wireless, fiber optics, etc...These are the different venues of communication that Ethernet supports.
-----
Now let us discuss the CSMA/CD which are the set of rules governing how you talk on an Ethernet network. After all, just like a real life meeting at work, there are rules on how you speak to such a network.
Every part of the network, such as PC, switch, even the layer 2 portion of the router, have to be able to correctly interact with an Ethernet network.
Let's go over them, shall we?
The rules are called the CSMA/CD standard. The acronym CSMA/CD stands for:
- Carrier: The network signal. This just means that there is going to be signals sent on Ethernet.
- Sense: The ability for all the members of a network to determine whether or not there is a Carrier signal at a given time. The real life equivalent is to imagine yourself in a meeting at work. You must be able to 'sense' that someone is talking and therefore wait for them to finish before you can say anything.
- Multiple Access: All devices have equal access. There is no favoritism here! Just gotta wait till its quiet on the network before you can say anything out loud.
- Collision: What happens if two devices send at once? Two people 'sensed' that it was safe to send out something on the network at the same moment in time.
- Detection: How the computers will handle collisions when they happen.
Now let's move onto the methods of communicatino that can take place on Ethernet. This is fairly straightforwad, so you can relax a bit.....Not that today's session has been difficult.
Anyway, let's begin with term known as Unicast. Here is a visual on what take place during a unicast message:


Here, the computer marked with 172.16.1.11 can use a switch to directly send a packet over to 172.16.1.10. This should be straightforward.
Now the Broadcast form of communication just means that the packet will go to every destination on the network (excluding the one who sent it). It's just the opposite of unicast.
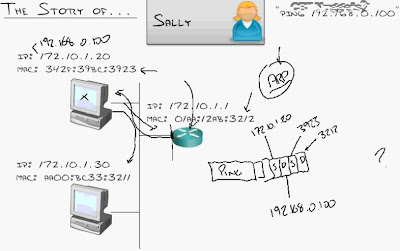
A good example of a broadcast message is the ARP protocol we were discussing earlier. An ARP request is sent to everyone on the network, so that the member with the matching IP address can reply with their MAC address.
Here is a visual:

Notice here that the packet sent out by 172.16.1.11 is sent out to the switch as a broadcast message. The switch will then in turn flood all its ports with that message to all other members on that network. However it is important to note that the switch will NOT send this packet out back to the originating machine.
The last type of communication we'll cover is Multicast. Think of it as a 'special people's club' message. Its meant only for a subset of people on the network.

As you can see that as the host machine sends the multicast message out onto the switch, the data only goes to 2 out of the 3 other network members.
Different applications use different forms of communication for different purposes.
-----
Lastly, let us discuss the official explanation of the MAC address. We've used them a lot, but we havent' gone into the gritty details.
We discussed the octets and the different classes of IP addresses, but now is where we will go into the construction of the MAC address.

First, its important to note that the MAC address has 12 characters. That is how long they are.
Furthermore MAC address characters are each hexadecimal. This means they have the range of 0-9 or A-F.
The left most 24 bits of the MAC address are known as the "Organizational Unique Identifier" or the OUI.
Since each hex character needs 4 bits to represent itself, that means that the first 6 characters of the MAC address (24 bits) represent this.
The OUI is part of a range of addresses that manufacturers register for in order to use for their devices.
For example in the image above, this vendor is allowed to use 00:19:D1 as OUI portion of the MAC address for all network devices they manufacturer.
Some OUI addresses are well known and you can see what manufacturer is responsible for making your network card by plugging in your network card's MAC address at
http://www.coffer.com/mac_find/
The second half of the MAC address is left up to the manufacturer to assign for their devices.
And that's it for today....short and sweet.